获取远端系统信息的工具
OSquery
简介
osquery是Facebook开源的SQL驱动操作系统检测和分析工具。osquery支持像SQL语句一样查询系统的各项指标。它使得底层操作系统分析和监控性能更加直观。
支持操作系统
- Windows
- OS X
- Linux
- FreeBSD
实际测试发现2.3.2版本在Windows 7和CentOS 7上可用。而且没有要求安装任何依赖。
CentOS, Ubuntu LTS, Windows, and OS X are supported with no dependencies
规格
支持查询的操作系统相关的表项:
| Table | description | PlatForm |
|---|---|---|
| arp_cache | Address resolution cache, both static and dynamic (from ARP, NDP). | ALL |
| carbon_black_info | Returns info about a Carbon Black sensor install | ALL |
| chrome_extensions | Chrome browser extensions. | ALL |
| cpuid | Useful CPU features from the cpuid ASM call. | ALL |
| etc_hosts | Line-parsed /etc/hosts. | ALL |
| etc_protocols | Line-parsed /etc/protocols. | ALL |
| etc_services | Line-parsed /etc/services. | ALL |
| hash | Filesystem hash data. | ALL |
| interface_addresses | Network interfaces and relevant metadata. | ALL |
| interface_details | Detailed information and stats of network interfaces | ALL |
| kernel_info | Basic active kernel information | ALL |
| listening_ports | Processes with listening (bound) network sockets/ports | ALL |
| logged_in_users | Users with an active shell on the system | ALL |
| os_version | A single row containing the operating system name and version. | ALL |
| platform_info | Information about EFI/UEFI/ROM and platform/boot. | ALL |
| process_open_sockets | Processes which have open network sockets on the system. | ALL |
| processes | All running processes on the host system. | ALL |
| system_info | System information for identification. | ALL |
| uptime | Track time passed since last boot. | ALL |
| users | Local system users. | ALL |
| appcompat_shims | Application Compatibility shims are a way to persist malware. This table presents the AppCompat Shim information from the registry in a nice format. http://files.brucon.org/2015/Tomczak_and_Ballenthin_Shims_for_the_Win.pdf | Windows |
| drivers | Lists all installed and loaded Windows Drivers and their relevant data | Windows |
| patches | Lists all the patches applied. Note: This does not include patches applied via MSI or downloaded from Windows Update (e.g. Service Packs). | Windows |
| programs | Rrepresents products as they are installed by Windows Installer. A product generally correlates to one installation package. | Windows |
| registry | All of the Windows registry hives. | Windows |
| services | Lists all installed Windows Services and its relevant data | Windows |
| shared_resources | Displays shared resources on a computer system running Windows. This may be a disk drive, printer, interprocess communication, or other sharable device. | Windows |
| windows_events | All of the Windows events. | Windows |
| wmi_cli_event_consumers | WMI CommandLineEventConsumer, which can be used for persistance on Windows. https://www.blackhat.com/docs/us-15/materials/us-15-Graeber-Abusing-Windows-Management-Instrumentation-WMI-To-Build-A-Persistent%20Asynchronous-And-Fileless-Backdoor-wp.pdf | Windows |
| wmi_event_filters | Lists WMI event filters | Windows |
| wmi_filter_consumer_binding | Lists the relationship between event consumers and filters. | Windows |
| wmi_script_event_consumers | WMI ActiveScriptEventConsumer, which can be used for persistance on Windows. https://www.blackhat.com/docs/us-15/materials/us-15-Graeber-Abusing-Windows-Management-Instrumentation-WMI-To-Build-A-Persistent%20Asynchronous-And-Fileless-Backdoor-wp.pdf | Windows |
因为主要考虑在Windows上使用osquery,此处都是列出的Windows系统支持的所有的表项和相关的说明。
说明
优势
- 通过sql语言操作和展示结果,用户界面比较友好
- OSquery 对不同的操作系统支持得较好,可以对不同的操作系统进行处理,兼容性较好。
- 通过C语言编写,基本没有依赖,便于移植。
- 支持和不同的log系统对接,比如ELK,便于扩展。
劣势
- 需要在endpoint上安装agent,不便于部署
示例
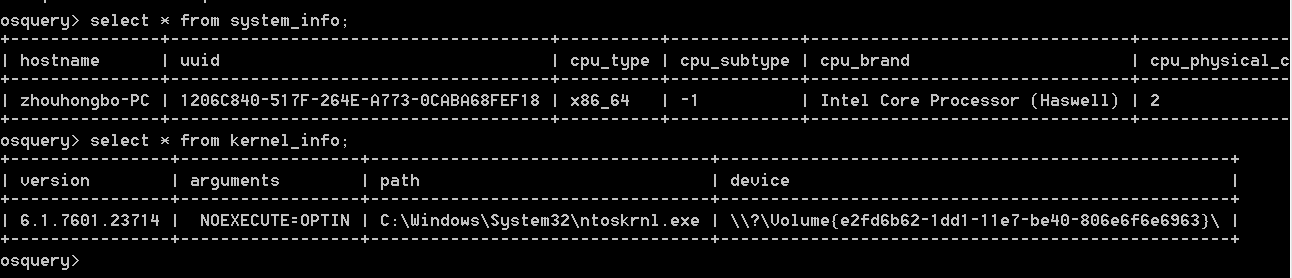 osq1.PNG-14.1kB
osq1.PNG-14.1kB
PSHunt
简介
PSHunt is a Powershell Threat Hunting Module designed to scan remote endpoints* for indicators of compromise or survey them for more comprehensive information related to state of those systems (active processes, autostarts, configurations, and/or logs).
PSHunt began as the precurser to Infocyte's commercial product, Infocyte HUNT, and is now being open sourced for the benefit of the DFIR community.
规格
PSHunt is divided into several modules, functions, and folders. The below gives an outline of the grouping of these functions and upcoming posts will describe how how to use them with examples and screenshots.
Discovery
Discovery functions and cmdlets are used to identify hosts on the network and build a target list that can be ingested by the scanners and survey deployment cmdlets.
Get-HuntTargets Invoke-HuntPortScan
Scanners
Scans are modular queries that take in a remote ComputerName argument and output a Powershell object. The utility Invoke-HuntScan is used to initiate the selected scan against your target list.
Scan_OSInfo.ps1
Surveys
Surveys are scripts that are deployed to remote hosts to collect comprehensive information from the host. Running locally allows the scripts to dig deeper into the operating system than what remote WMI or registry queries normally allow.
Survey.ps1 SurveyLogs.ps1
Utilities
Utility functions provide the base functionality for deployment and execution of surveys and scans.
Invoke-HuntSurvey Get-HuntSurveyResults Invoke-HuntScanner
Analysis
There are two types of analysis functions:
- Survey Analysis
Survey Analysis functions provide the framework for analysing and displaying survey and scan results.
Initialize-HuntReputation Update-HuntObject Group-HuntObject
- File Analysis
File Analysis functions are a set of utilities to analyze files and malware.
Get-Entropy Get-VTReport Get-Hashes
Libraries (Lib)
Libraries are 3rd party tools that have been incorporated to enable additional analysis or are other projects (i.e. Posh-VirusTotal) that are utilized by the framework.
7zip Posh-VirusTotal
Reputation Lists
Reputation lists include hashes from the NIST NSRL Database, baselined virtual machines provided by Infocyte, and also is updated with any VirusTotal submission made using PSHunt's Get-VTReport. These lists are loaded into a global memory variable by Initialize-HuntReputation and is compared against by Update-HuntObject.
说明
PSHunt是基于Powershell的项目。从目前的分析来看,整个项目主要使用了WMI技术
什么是WMI
使可扩展的基于架构模式的管理简易化
The model is based on the Common Information Model (CIM), which forms part of the WBEM standard owned by the Distributed Management Task Force (DMTF).
提供了丰富的事件和查询管理服务集
简化易用的WQL,是一种类SQL的语言,能够查询特殊的数据
Remote-enable
提供远程的数据能力
Scriptable
提供一个scripting api接口
安装
可以通过powershell来安装PSHunt,在github上下载之后,将整个目录拷贝到系统缺省的module目录:
C:\Users\zhouhongbo\Documents\WindowsPowerShell\Modules\
然后在powershell中通过如下命令安装:
Import-Module -Name PSHunt
安装完之后就可以使用上面介绍的类似于Get-HuntTargets这样的命令了,如果对指定的命令不熟悉,可以通过get-help Command来查看帮助信息。
优势
- 通过scann的方式来获取系统信息,不用在每一台endpoint上安装agent
- 使用WMI的技术,通用性好,便于对所有的Windows系统进行管理。
- 通过Powershell的方式,对Windows支持得较好。
劣势
- 只支持对Window PC进行扫描和管理
- 作为管理服务器部署时不好部署(powershell是windows程序,现在服务器一般都是Linux)
- 较少人使用,脚本错误比较多(在使用的时候修改了好几处,脚本才能跑得起来,比如把keyvalue写成keyvalue;或者输出的字符串少了“”,被当做命令来执行了。)
示例
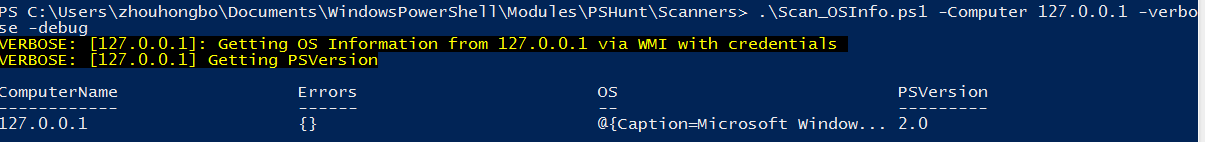 pshunt1.PNG-13.6kB
pshunt1.PNG-13.6kB
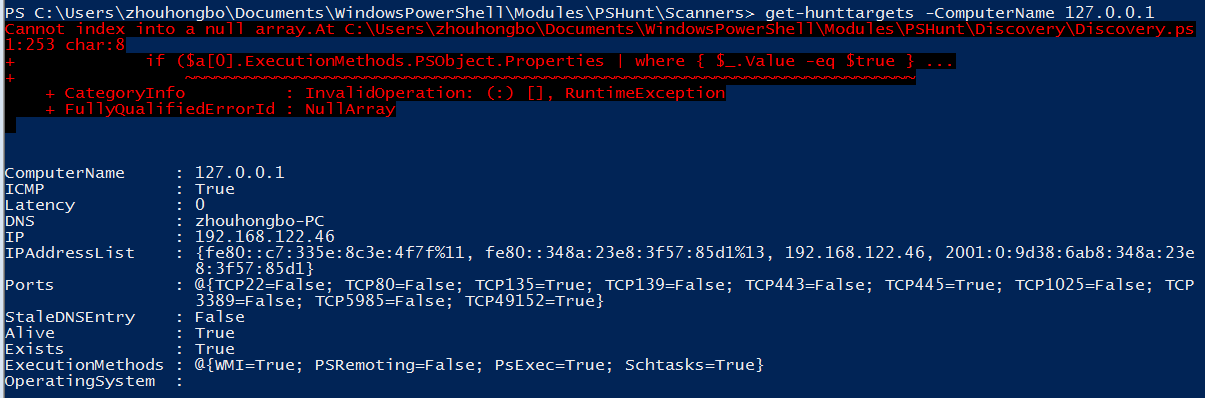 ps2.PNG-35.4kB
ps2.PNG-35.4kB
备注
如果需要通过远程访问的方式使用WMI,需要在Windows机器上做如下配置:
开启WMI和RPC服务
Remote Procedure Call (RPC)
Remote Procedure Call (RPC) Locator
Windows Management Instrumentation
添加管理账户
右键我的电脑/管理/展开服务和应用程序/右键WMI/属性/安全页签/选择CIMV2目录/点击安全设置加入相关账号
解决拒绝访问的问题(异常来自 HRESULT:0x80070005 (E_ACCESSDENIED))
解决方法:
- 检查HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa下的forceguest的值.该值必须为0(dword:00000000)
- 单击“开始”,单击“运行”,键入 DCOMCNFG,然后单击“确定”。在“组件服务”对话框中,依次展开“组件服务”、“计算机”,然后展开“我的电脑”。在工具栏上,单击“配置‘我的电脑’”按钮。随即显示“我的电脑”对话框。在“我的电脑”对话框中,单击“COM 安全”选项卡.在“启动和激活权限”下,单击“编辑限制”。在“启动权限”对话框中,如果您的名称或您的组未显示在“组或用户名称”列表中,请按照下列步骤操作:
- 在“启动权限”对话框中,单击“添加”。
- 在“选择用户、计算机或组”对话框中,将您的名称和组添加到“输入对象名称来选择”框中,然后单击“确定”。 在“启动权限”对话框中,在“组或用户名称”框内选择您的用户和组。在“用户权限”下的“允许”栏中,选择“远程启动”,然后单击“确定”。
运行wmimgmt.msc可以查看wmi连接情
WMIC
简介
WMIC扩展WMI(Windows Management Instrumentation,Windows管理工具) ,提供了从命令行接口和批命令脚本执行系统管理的支持。在WMIC出现之前,如果要管理WMI系统,必须使用一些专门的WMI应用,例如SMS,或者使用WMI的脚本编程API,或者使用象CIM Studio之类的工具。如果不熟悉C++之类的编程语言或VBScript之类的脚本语言,或者不掌握WMI名称空间的基本知识,要用WMI管理系统是很困难的。WMIC改变了这种情况。
WMIC是一个WMI的一个客户端,允许用户通过WQL来管理WMI,WQL是一种类似于sql的查询语言,便于用户将复杂的WMI命令简化为清晰的sql语言来处理。
说明
优势
- 使用WMI的技术,通用性好,便于对所有的Windows系统进行管理。
- WMIC有不同系统的版本,支持Linux,便于部署。
- WMIC有不同语言的版本,如Python,便于扩展和二次开发。
劣势
- Linux版本的WMIC可能功能略少,不如Windows版本强大。
示例
获取IP地址
[root@forti-zhbo wmic]# wmic -U zhouhongbo%123 //192.168.122.46 'SELECT IPAddress FROM Win32_NetworkAdapterConfiguration'
CLASS: Win32_NetworkAdapterConfiguration
Index|IPAddress
0|(null)
CLASS: Win32_NetworkAdapterConfiguration
Index|IPAddress
1|(null)
CLASS: Win32_NetworkAdapterConfiguration
Index|IPAddress
2|(null)
CLASS: Win32_NetworkAdapterConfiguration
Index|IPAddress
3|(null)
CLASS: Win32_NetworkAdapterConfiguration
Index|IPAddress
4|(null)
CLASS: Win32_NetworkAdapterConfiguration
Index|IPAddress
5|(null)
CLASS: Win32_NetworkAdapterConfiguration
Index|IPAddress
6|(null)
CLASS: Win32_NetworkAdapterConfiguration
Index|IPAddress
7|(192.168.122.46,fe80::c7:335e:8c3e:4f7f)
CLASS: Win32_NetworkAdapterConfiguration
Index|IPAddress
8|(null)
CLASS: Win32_NetworkAdapterConfiguration
Index|IPAddress
9|(null)
CLASS: Win32_NetworkAdapterConfiguration
Index|IPAddress
10|(null)
CLASS: Win32_NetworkAdapterConfiguration
Index|IPAddress
11|(null)
CLASS: Win32_NetworkAdapterConfiguration
Index|IPAddress
12|(null)
获取系统信息
[root@forti-zhbo wmic]# wmic -U zhouhongbo%123 //192.168.122.46 'select * from win32_operatingsystem'
CLASS: Win32_OperatingSystem
BootDevice|BuildNumber|BuildType|Caption|CodeSet|CountryCode|CreationClassName|CSCreationClassName|CSDVersion|CSName|CurrentTimeZone|DataExecutionPrevention_32BitApplications|DataExecutionPrevention_Available|DataExecutionPrevention_Drivers|DataExecutionPrevention_SupportPolicy|Debug|Description|Distributed|EncryptionLevel|ForegroundApplicationBoost|FreePhysicalMemory|FreeSpaceInPagingFiles|FreeVirtualMemory|InstallDate|LargeSystemCache|LastBootUpTime|LocalDateTime|Locale|Manufacturer|MaxNumberOfProcesses|MaxProcessMemorySize|MUILanguages|Name|NumberOfLicensedUsers|NumberOfProcesses|NumberOfUsers|OperatingSystemSKU|Organization|OSArchitecture|OSLanguage|OSProductSuite|OSType|OtherTypeDescription|PAEEnabled|PlusProductID|PlusVersionNumber|Primary|ProductType|RegisteredUser|SerialNumber|ServicePackMajorVersion|ServicePackMinorVersion|SizeStoredInPagingFiles|Status|SuiteMask|SystemDevice|SystemDirectory|SystemDrive|TotalSwapSpaceSize|TotalVirtualMemorySize|TotalVisibleMemorySize|Version|WindowsDirectory
\Device\HarddiskVolume1|7601|Multiprocessor Free|Microsoft Windows 7 | 936|86|Win32_OperatingSystem|Win32_ComputerSystem|Service Pack 1|ZHOUHONGBO-PC|480|True|True|True|2|False||False|256|2|1608444|4121988|5498080|20170410174446.000000+480|0|20170417094355.357421+480|20170417185937.089000+480|0804|Microsoft Corporation|0|8589934464|(??-??,??-??)|Microsoft Windows 7 |C:\Windows|\Device\Harddisk0\Partition2|0|85|0|1||64-bit|2052|256|18|(null)|False|(null)|(null)|True|1|zhouhongbo|00426-292-0000007-85071|1|0|4193904|OK|272|\Device\HarddiskVolume2|C:\Windows\system32|C:|0|8385948|4193904|6.1.7601|C:\Windows


